What is Z-Wave? How Z-Wave Works?
What is Z-Wave? How Z-Wave Works?
What is Z-Wave? How Z-Wave Works?
How Z-Wave works
Using source-routed mesh network technology, Z-Wave signals can hop through other Z-Wave devices to reach the device a user intends to control. Each Z-Wave network accommodates a maximum of four hops.
The Z-Wave protocol operates on the low-frequency 908.42 band in the U.S. and the 868.42 MHz band in Europe. Though interference with other home electronics, such as cordless phones, is possible, the protocol avoids interference with the 2.4 GHz band where Wi-Fi and Bluetooth operate.
Z-Wave offers transmission rates of small data packets using throughput rates of 9.6 kbps, 40 kbps or 100 kbps. The Z-Wave PHY and MAC layers are based on the ITU-T G.9959 global radio standard, and the protocol uses GFSK modulation and Manchester encoding. It also includes AES 128 encryption, IPv6 and multichannel operation.
In terms of identification and authorization, each Z-Wave network is identified by a network ID and each end device is identified with a node ID. The unique network ID prevents, for example, one Z-Wave-equipped house from controlling devices in another similarly equipped house.
Communication between devices ranges from 98 to 328 feet; the 500 Series has a range of 130 feet and the 700 Series 328 feet. Because walls and other dense building materials limit the range, the general deployment best practice is to place Z-Wave devices 50 feet or fewer apart for maximum signal strength.
Using a Z-Wave repeater — an additional Z-Wave device between other devices — or using line-powered — not battery-powered — devices in the network can also strengthen the signal and help it reach its destination. The maximum range with four hops is estimated to be 600 feet.
In regards to battery life, some 700 Series Z-Wave devices can last up to 10 years on a coin cell battery, while many other battery-powered devices last a year or longer.
All Z-Wave technology is backward-compatible.
To bear the Z-Wave branding, smart home products must become Z-Wave certified. This involves meeting a number of requirements and, most importantly, being interoperable with all other Z-Wave-certified devices.
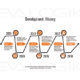
History
First envisioned by Danish company Zensys, the Z-Wave protocol began as a light-control system for consumers and evolved into a home automation network mesh protocol implemented on a proprietary system-on-a-chip (SoC). The company aimed to make a simpler, less expensive alternative to existing smart home protocols. Zensys was acquired by Sigma Designs Inc. in 2008.
In 2001, the 100 Series chipset was released, followed by the 200 Series in 2005. In 2013, the 500 Series, also known as Z-Wave Plus, was released, offering a 50% improvement in battery life, 67% improvement in range and 250% more bandwidth, as well as plug-and-play capabilities and standardized, over-the-air updates.
The Z-Wave Alliance, a consortium of industry leaders, manufacturers and integrators aimed at developing and expanding Z-Wave applications and capabilities. It was found in 2005 when members from Intermatic Inc., Leviton Manufacturing Co. Inc., Wayne Dalton, Danfoss and Universal Electronics met with Zensys to discuss the state of home automation protocols. The more than 700 current members include D-Link Systems Inc., Honeywell International Inc., LG Electronics and Verizon, among others.
In 2016, some Z-Wave technology was made open source. Sigma Designs added an interoperability layer to the Z-Wave open source library with the aim to give software developers, manufacturers, hobbyists and academics, among others, the ability to read, use and comment on how Z-Wave works without joining the Z-Wave Alliance or purchasing a Z-Wave development kit. Prior to this, nondisclosure agreements were required, and the specifications were only available to Z-Wave Alliance members and Z-Wave development kit holders.
Sigma Designs also released the Z-Wave S2 security specification, the Z-Wave over IP Specification for transporting Z-Wave signals over IP networks and Z-Ware middleware in 2016.
In 2017, Sigma Designs announced Z-Wave SmartStart, a combination of the Z-Wave protocol and Z-Wave gateway software layers. Allowing for preconfiguration and eliminating the need to manually add devices to a Z-Wave home network, as they can automatically connect when powered on.
Z-Wave adoption and popularity
In 2002, a reported six Z-Wave-certified devices were available on the market. In 2012, that number rose to 1,000. Currently, in 2018, more than 2,400 Z-Wave-certified devices are available from the more than 700 members of the Z-Wave Alliance.
Z-Wave’s website claims it has the largest selection of smart products available across widely recognize brands, and that more than 100 million Z-Wave protocols sold for smart homes worldwide.
Today, Z-Wave-certified devices are used for remote control and management in a variety of. For example smart home including smart thermostats, smart locks, smart lighting, smart sensors, smart plugs and outlets.
Z-Wave-certified products are available from brands including ADT, GE, Honeywell, Kwikset, Schlage and SmartThings.
Z-Wave security
Early on, Z-Wave had a bad security reputation. While it offered AES encryption. There were a number of security incidents involving Z-Wave largely due to implementation errors. By manufacturers or manufacturers not using the recommend security in the first place.
In a 2013 Black Hat presentation, hackers demonstrated how to use the Z-Force packet interception and injection tool to identify a critical implementation vulnerability in the Z-Wave security layer. They showed how to compromise an AES-encrypted Z-Wave door lock. They turn out not to flaw introduce by Z-Wave, but by the door lock manufacturer. On response, Sigma Designs added additional security test cases to its certification processes.
In a 2016 ShmooCon presentation, two hackers demonstrated how the open source EZ-Wave penetration testing tool could be used to destroy lights and physically damage Z-Wave-certified devices. About their research, the hackers found that only nine of the 33 devices they tested supported AES. In turn, the Z-Wave Alliance made AES 128 encryption mandatory for a device to become certified.
The Z-Wave Alliance mandated Z-Wave-certified devices follow the Security 2 (S2) framework beginning in April 2017. This modified the process from a three-step process in the previous S0 framework to a one-step process in S2.
In an attempt to mitigate man-in-the-middle, distributed denial-of-service and brute-force attacks against Z-Wave devices, S2 uses elliptic curve Diffie-Hellman cryptography and requires a QR or PIN code at the device level for authentication. S2 also implements strengthened cloud communication by tunneling all Z-Wave over IP traffic through a secure TLS 1.1 tunnel.
In May 2018, researchers from Pen Test Partners found a five-year-old software vulnerability in the Z-Wave protocol dubbed Z-Shave, which affected an estimated 100 million SoCs in smart home devices manufactured by more than 2,400 vendors.
In the attack, one device is tricked into believing the other does not support Z-Wave’s S2 framework, so it downgrades the device’s security to the S0 framework for compatibility. As S0 uses a hardcoded encryption key, hackers in range can potentially intercept communication and smart lock keys to unlock home doors.
Silicon Labs refute the ability of the attack, claiming that this attack requires close physical proximity to the device during the pairing process is done during initial installation or reinstallation. This means the user would have to be present at the time of the attack and would be made aware of a device running S0. The company also state that it is updating the specification to ensure users get a warning any time a device is downgraded to S0. The user would have to acknowledge and accept the warning to run the system.
What is Z-Wave? How Z-Wave Works? So i think you should know after reading the article.